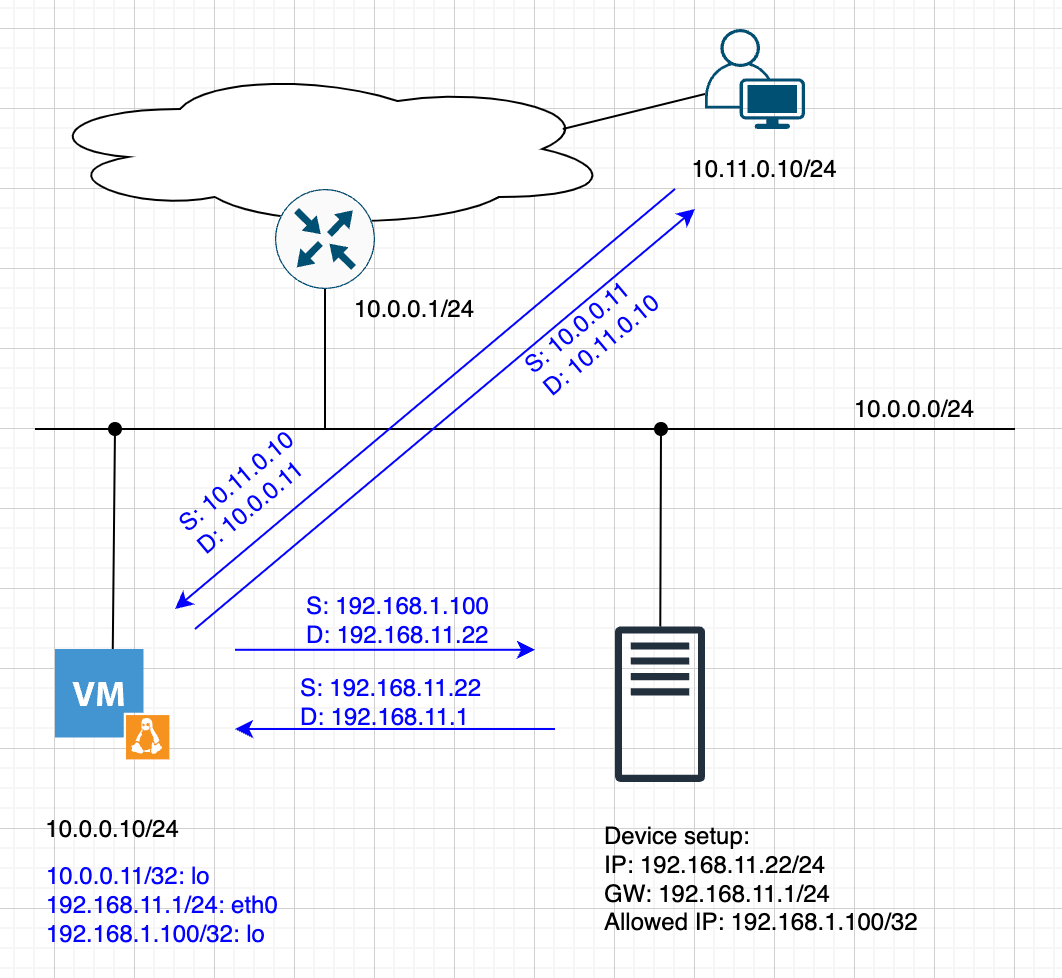
Imagine this case:
You have to access to the device with its own:
- IP address/mask
- gateway
- Access list restrict allowed IP
And, You cannot change any of this.
Something like this:
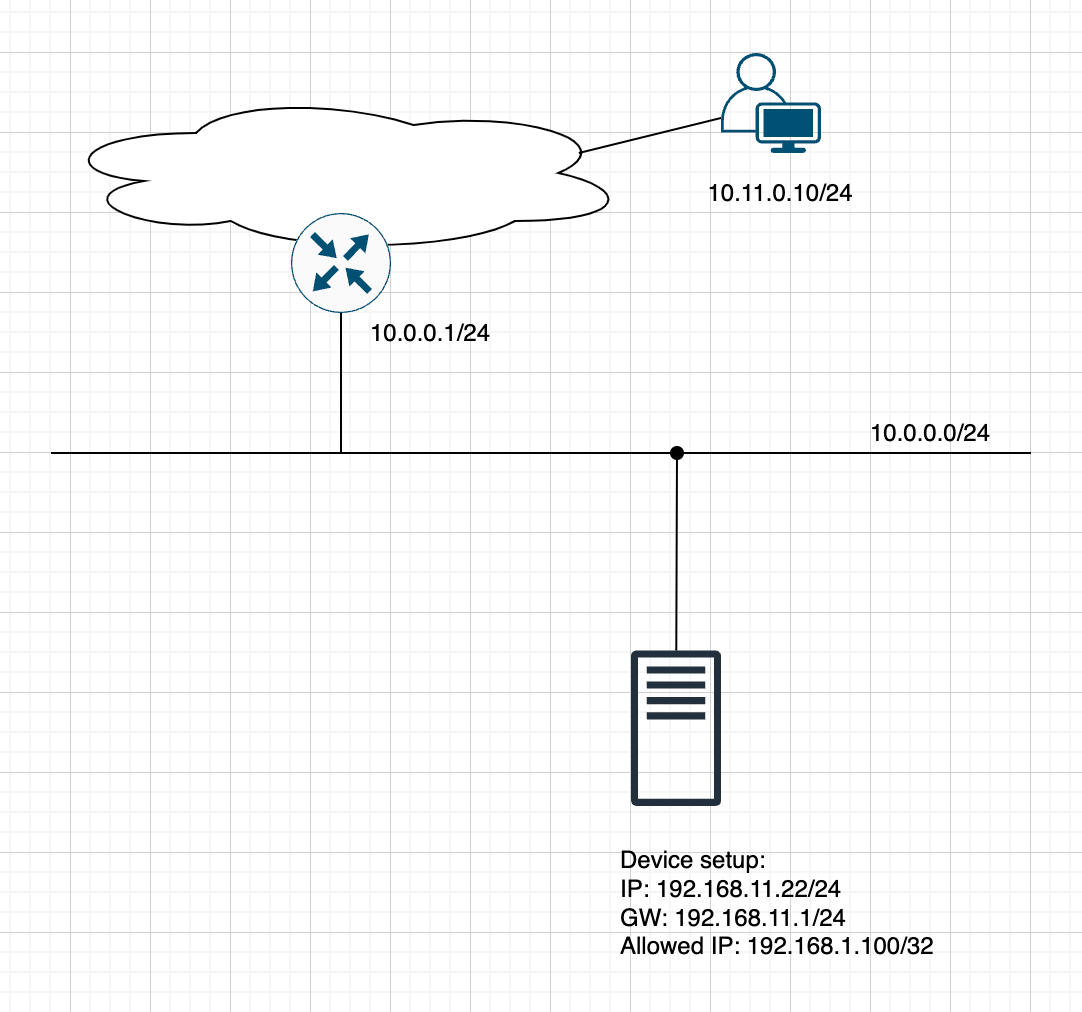
Obvious solution is to create custom network environment for it - secondary interface on router and NAT on router.
But It is not necessary to hassle with router. You can use much more elegant and safer solution with small alpine VM and do NAT here.
su
ip addr add 10.0.0.11/32 dev lo # here comes packet from user
ip addr add 192.168.11.1/24 dev eth0 # this is GW for Alien device
ip addr add 192.168.1.100/32 dev lo # IP allowed to manage Alien device
sysctl -w net.ipv4.ip_forward=1
# DNAT changes destination address from Loopback on Alpine to the real Alien device IP
iptables -t nat -A PREROUTING -d 10.0.0.11 -j DNAT --to-destination 192.168.11.22
# SNAT changes source address of packets going to allowed IP
iptables -t nat -A POSTROUTING -d 192.168.11.22 -j SNAT --to-source 192.168.1.100
And that is all. Now You can communicate from any host in your network to the new Alien device.
Like this: