This post includes important comments to the following LAB:
https://github.com/sbezo/linux-network-lab-2025.git
Motivation
It is more common to build IPSec on commercial products of known vendors. It is very well documented and almost no surprises here. And You have a support of course;).
But OpenSource is something different, and I wanted to test it…
It is interesting fact, that it is quite difficult to find such complete configuration for IPSec on Linux. I have found just partial configurations, or just IPSec with secret authentication, or mostly broken configurations. So I decided to build this complete LAB with demonstrable end-to-end connectivity.
I’d like to provide something ‘independent’ so no specific lab frameworks. The only prerequisite is docker.
I hope this is also very good start point for further investigation.
Technology stack
There are more frameworks for IPSec and networking handling in Linux of course. This time I choose:
- LibreSwan for IPSec
- FRR for Linux routing
Regarding IPSec I chose:
- modern ‘route based’ VPN with VTI - Virtual Tunnel Interface
- Authentication based on RSA Certificates
- BGP over IPSec is used to control routing between sites
- IKEv2 as control protocol for IPSec
Wrapping it to Docker
The most sexy part for me is a possibility to spin up whole LAB by simple docker compose up. It is still like a magic for me - who built labs for decades with physical HW and then hypervisors and different simulators looks like miracle. But speed and lightness of containerization technology is absolutely amazing.
There are only 4 important steps in whole LAB:
- Clone repository
- Create certificates (only once needed)
- Spin up docker containers
- Push whole configuration (linux + FRR) by one script
Now it is possible to play with configuration files of LibreSwan. After any change ipsec restart is needed. Or with FRR configuration.
And magic comes when you want to return to beginning for any reason. You can just run docker compose down and start from scratch with new LAB. Within few second you have fresh new LAB ready.
Certificates
Certificates part was quite surprisingly most tricky for me.
1. LibreSwan RSA implementation requires using of SAN (subject Alternative Name) in identity certificates. It didn’t want to work without SAN for me.
Because openssl doesn’t support signing CSR with SAN by default, I had to add some magic parameters during certificate creation.
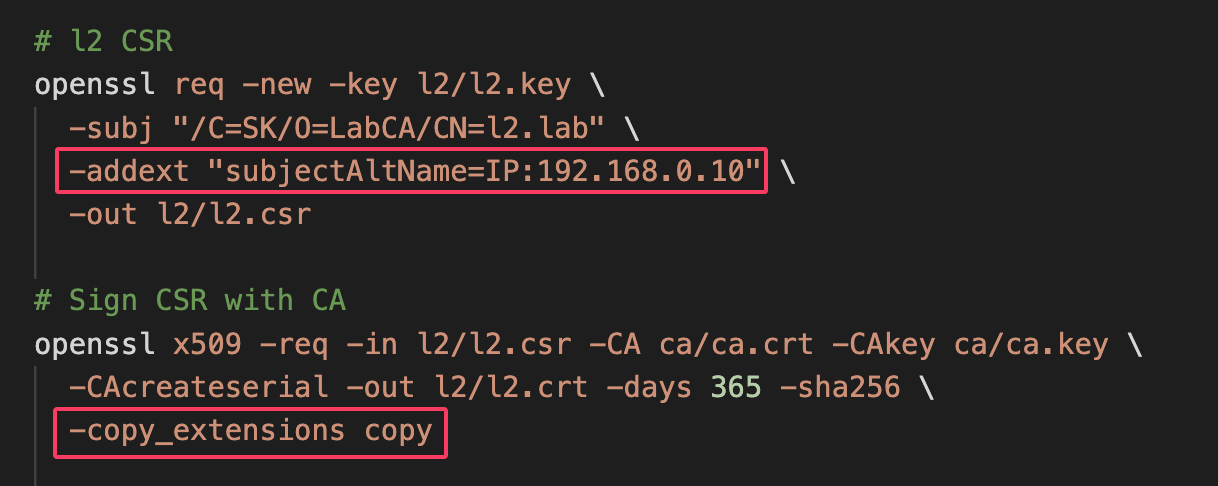
2. NSS (Network Security Services) library is mandatory for using with LibreSwan. I couldn’t make it work without it. So I had to install, initialize NSS first and then add certificates to NSS database.
So apt-get install libnss3-tools in Dockerfile and
ipsec initnss
pk12util -i /etc/ipsec.d/certs/l2.p12 -d sql:/var/lib/ipsec/nss -K "" -W ""
certutil -M -n "l2.lab" -t "CT,C,C" -d sql:/var/lib/ipsec/nss
certutil -A -n "LabRootCA" -t "CT,C,C" -d sql:/var/lib/ipsec/nss -i /etc/ipsec.d/cacerts/ca.crt
in ipsec configuration file linux_rsa.cfg
Then you can set and check IKE ID identities in LibreSwan configuration file:
leftid="@192.168.0.10"
rightid="@192.168.0.11"
Not sure about other possibilities, like checking SN of certificate, or parameters from FQDN. Documentation is not so clear. I’ll certainly test it later.
3. Certificate files are mapped within docker-compose.yml file
FRR
I played with Bird before, but I wanted to touch also FRR. It is pretty straightforward. Looks like Cisco CLI. And I had even better feeling than Bird.
Interesting is, that FRR itself doesn’t create interfaces (like vti01 in my case). You have to create them in Linux and FRR adopt them. The same for Loopbacks.
You can easily switch between linux bash and FRR by vtysh and exit inside docker. Or go directly to it from outside: docker exec -it l2 vtysh.
BGP
BGP part was also very intuitive.
router bgp 65501
neighbor 10.0.10.2 remote-as 65502
neighbor 10.0.10.2 ebgp-multihop 255
neighbor 10.0.10.2 update-source lo
neighbor 10.0.10.2 timers 5 20
!
address-family ipv4 unicast
network 10.0.1.0/24
redistribute connected
neighbor 10.0.10.2 soft-reconfiguration inbound
neighbor 10.0.10.2 route-map RM-IN in
neighbor 10.0.10.2 route-map RM-OUT out
The only small catch was, that it doesn’t want to propagate routes without route-maps.
Conclusion
There are probably a lot of things to explain or discuss regarding current setup. This lab is not meant as a full tutorial but as a working foundation. It should give you a ready-to-use base for experimenting and extending IPSec with LibreSwan and BGP on Linux.
My goal is not to explain everything in detail, but provide working solution as a base for further individual exploration. And as this is my personal blog, I commented what I found to be interesting for me;).